Building an ICS Lab

BackStory
So you want to build an ICS lab?
When I started down the path of ICS Security one of my questions was “how to I practice?” It wasn’t until I went to the SANS ICS Summit that I received an answer. Thanks to the staff at GRIMM, SANS, Dragos, and TCM Security I was able to put together my comprehensive ICS Practice Lab. What you will need:
- PLC
- Engineer Work Station (EWS)
- Human Machine Interface (HMI)
- Historian
- ICS Specific Traffic
- Monitoring and forensic tools
- Malware Analysis
My Lab
LEvel 4 & 5: Malware Analysis/ Host Intrusion Detection System (HIDS)
Flare VM
When doing static analysis you need a vm to…abuse. Created by the team at Mandiant, Flare VM is the platform that I use detonate and examine malware samples.
- FLOSS
- peid
- CFF Explorer

Level 4 & 5: Malware Network Analysis / Network Intrusion Detection (NIDS)
REMnux
My Flare VM is connected to REMnux VM for simulating and tracking web traffic of malware.
- Burp Suite
- Network Miner
- INetSim
- Wireshark

Level 3.5: DMZ/ Firewall/ Honeypot
PFSense
PFSense is a great firewall…setup can be a complete pain in the everything, but, when it’s up adding Suricata is a simple addon.
- Protectli Hardware
- Suricata
Level 3: Engineer Workstation / Historian
Windows 10 ICS
Created by the SANS Institute of Technology team, this Windows 10 VM is created to mimic a typical engineer workstation. Other useful DFIR tools are included like Wireshark and Notepad++.
- Run HMI
- Click PLC
- Wireshark
- Notepad ++
- Marticon OPC Services for Modbus
- CLICK PLC Programmer

Level 2: HMI / ICS TRAFFIC / ICS forensic tools
Relics / Dragos
Also, from the SANS Team this custom Linux VM is responsible for providing and interface for PLCs. I have also stored DFIR and SEIM tools on this VM.
- Suricata
- Snort
- Yara
- Volitility
- PLC Connection / Traffic
- ELK

Level 1: PLC
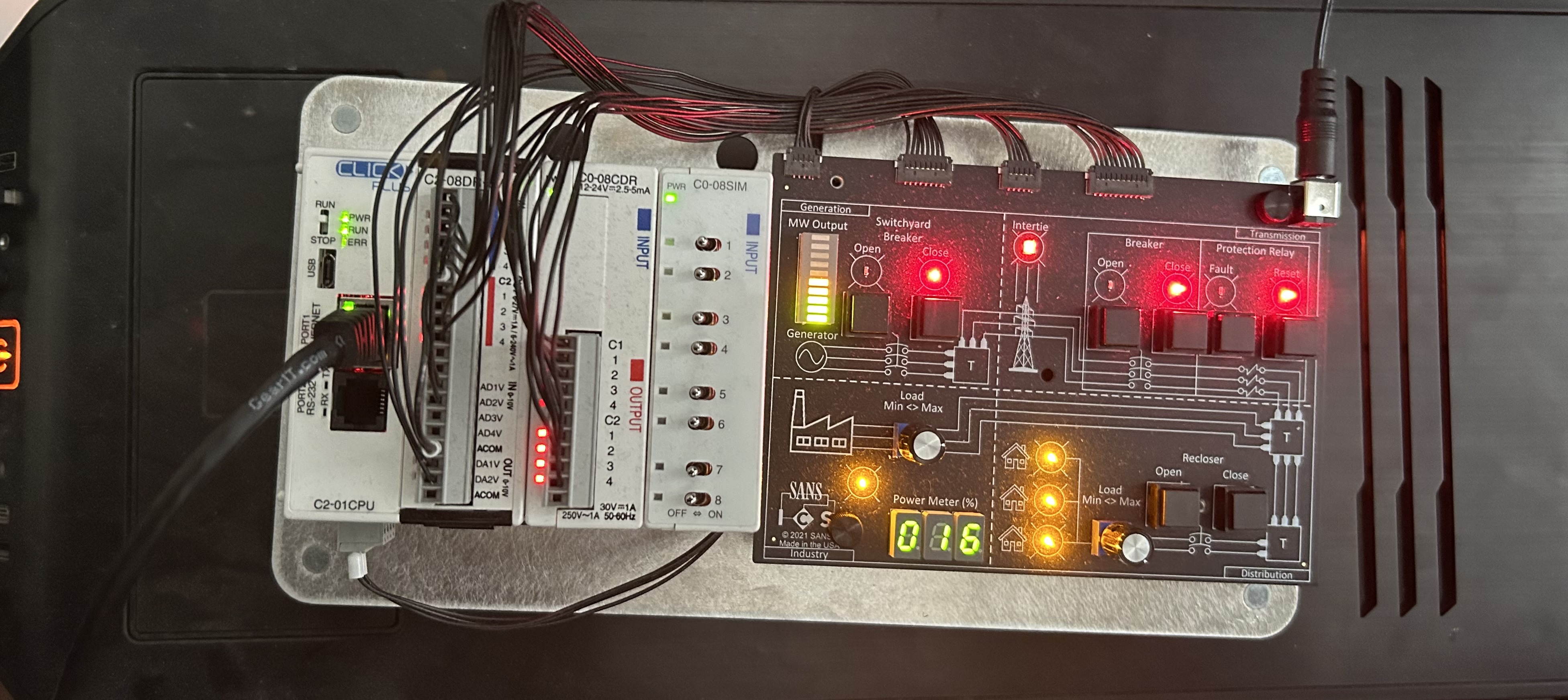
CLICK Plus
A part of the SANS ICS 515 training is assembling a CLICK PLC. This provides a way to physically interact with a power grid.
- Generation: Switchyard Breaker
- Transmission: Breaker, and Protection Relays
- Residential: Breakers, and Min-Max Load Dial
- Industrial: Breakers an, Min-Max Load Dial